In the past there was a program called True Crypt that used to do advanced encryption. Unfortunately, during an inspection by the company there were a number of security issues in the program and some vulnerabilities so the program was scrapped.
VeraCrypt
Enter VeraCrypt, the drop in replacement for True Crypt. VeraCrypt fixed all the problems in True Crypt and improved the product.
VeraCrypt is a free Open Source disk encryption program.
Containers
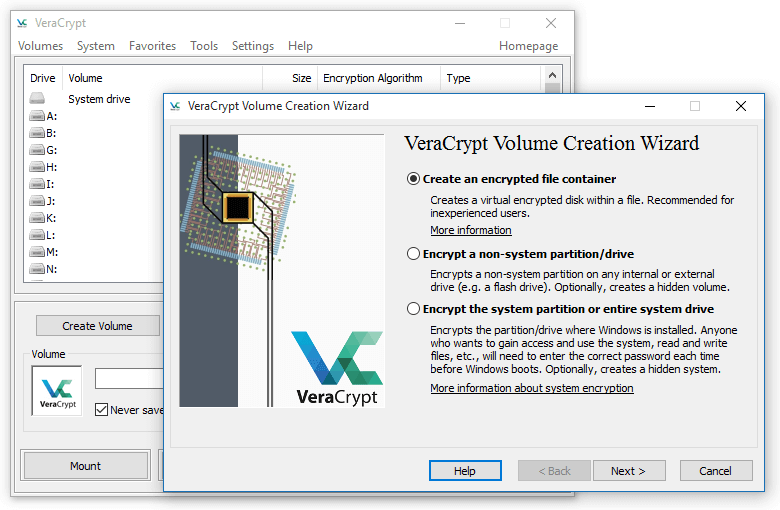
One way to use VeraCrypt is by creating a container on your computer that is encrypted and you mount with a drive letter.
When you mount the container, you enter a password to unlock it. You can then treat it like a storage drive. You can open, read and write to it as if it is part of your computer, then you can unmount it and the content of the container file is unreadable to anyone who doesn’t have the password.
Encrypted Drives
In addition to Virtual Volumes, VeraCrypt can be used to encrypt an entire drive, such as a memory stick or external drive. This means that the drive is treated like a normal memory stick once the password has been entered, but is unreadable if someone doesn’t know the password.
System Encryption
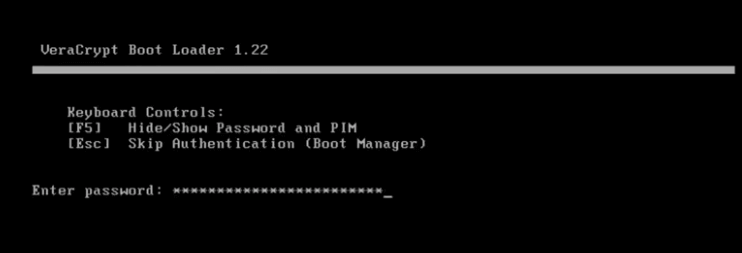
VeraCrypt can be set to encrypt the Windows installation partition, which means the area of the drive where Windows is installed is encrypted with a password but the boot area is not, which makes it easier to repair Windows, but could be used to wipe the drive. Either with a copy that is unencrypted or a separate Windows installation that has a different password.
Alternatively, the entire drive can be encrypted. You can opt to decrypt the entire drive once it has been encrypted.
Once your computer restarts, you will be presented with a screen asking for your password, as well as a PIM, if set. The Personal Iterations Multiplier or PIM is the number of iterations that is used to harden the password you have chosen. By default, if your password is less than 20 characters, it is set to 98. If you have a longer password, then you can set your own PIM. The larger the number, the more secure the password becomes but the slower decryption becomes. It is optional, but when enabled the correct PIM must be entered along with the correct password or the system will not boot. Note that the US keyboard is used, so any non US keys may prevent login, and some symbols may be located in the wrong places on the keyboard.
Plausible Deniability
If you wish to prevent an adversary from forcing you to reveal your data, you can do a number of things with VeraCrypt:
- Create hidden volumes – The volume can contain an additional hidden volume with a different pass word to the main volume, this volume is hidden inside and will not be visible to the adversary.
- Create hidden operating system – This involves creating a decoy operating system with a different password to the hidden operating system, and when the decoy is booted it has no access to the hidden operating system. However, the decoy operating system must be used much more frequently than the hidden one, as that will allay suspicions that you have something hidden.
Operation
VeraCrypt is transparent and the encryption/decryption process happens in real time, with all encrypted data being transferred to and from the drive at the same speed as unencrypted data.
Passwords can contain spaces and can be as long as you want. They could be a song you remember from childhood with the punctuation you like, but remember that the US keyboard will be used, so avoid non-US symbols and some symbols may not be available or in the right places, namely: “£@’~#\ as these are common pitfall symbols.
Android and iOS
Although VeraCrypt does not run on Android or iOS, there are some clients that allow the containers to be opened.
A container can be stored on the cloud storage such as Google Drive or iCloud and the container can be mounted and accessed from the device, enabling your smart phone or tablet to access files and folders in encrypted containers anywhere in the world and the data is kept secure from prying eyes.
Download
Veracrypt is available for Windows, Mac and Linux from veracrypt.fr


