I was called out to a customer who had been scammed, but what I found was something much worse. Scammers are now using techniques gained from an Iranian cyberespionage group called MuddyWater or Static Kitten to breach the security and install a backdoor into the customer’s computer.
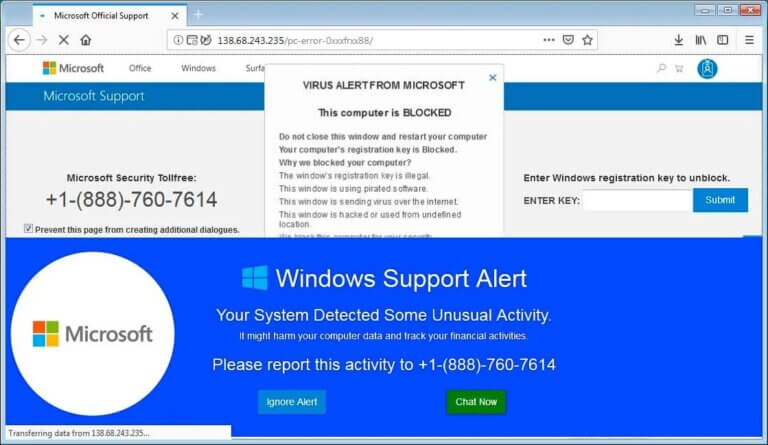
1. Fake Virus Scare
The customer was looking for her grocery store online and clicked on a link in Bing that looked like it was the grocery store, this turned out to redirect to a fake virus page that looked like Windows Defender had found some malware that contained some loaded phrases like pornography to scare the customer into calling their number. There was a recorded voice and filled the screen so it looked genuine to the customer.
She called the number and they logged into her computer to “fix” it and then tried to get into her online banking, which she doesn’t have, so they tried the e-card route for payment.
2. The e-Card scam
They convince the victim to pay them with e-Cards that add up to the value they are extorting them with.
The scammer feeds these e-Cards into an exchange site which converts their value into cryptocurrency so they can launder the e-Cards to make them untraceable. The cryptocurrency is then converted into real currency and they get roughly half the value of them, but to them it’s free money. They give each other a glowing report which encourages more people to use their services.
3. The Deployment payload
The scammers installed their remote access tool, but they also installed a backdoor program so they could access the computer without the customer’s knowledge. In the case of this customer, she got her money back and stopped the money leaving her accounts, however they had the ability through the backdoor to install fake virus programs and other tools such as ransomware.
The Callout
The scam was pulled on Saturday and I started working on the computer on Monday. My scan tools missed the backdoor, but I noticed some strange things happening, which were common for cordless mice and keyboards when the batteries start to fail until a blue screen appeared with Windows installing updates, but the font was wrong and I notice the mouse cursor move and change shape. I turned the computer off and then the router, powered the computer back on and performed a Windows Reset saving files.
Since it was late and the computer was slow as molasses it was going to go all night. This gave me the chance to download all the programs she uses to a memory stick on my home broadband and perform a clean install on her computer with those programs.
Solving the puzzle
The next day I could see what had happened to her computer:
- They connected using a common remote access tool.
- They downloaded what looked like an innocent Word document that had been weaponised to download a PowerShell script from github.
- They used a Cobalt Strike payload downloaded from an innocent looking image (the image contains text that tells the script where to get the hacker tools from)
- They deployed PDF dropper tools to compromise the security of the machine.
- They installed a remote management tool called ScreenConnect that opens a backdoor to the computer.
Using the Windows Reset tool with keep files enabled, it meant that Windows installed a clean copy and removed any installed programs, moving the user data out of the way to be recovered later. The deployment and payload was deployed into the AppData area because that cannot be set as a protected folder, but also means that to the careful eye, the puzzle can be unravelled.


