
Apps that steal your personal data
A couple of days ago Google pulled some apps that made use of a SDK (Software Development Kit) that harvested user data and sent it

A couple of days ago Google pulled some apps that made use of a SDK (Software Development Kit) that harvested user data and sent it
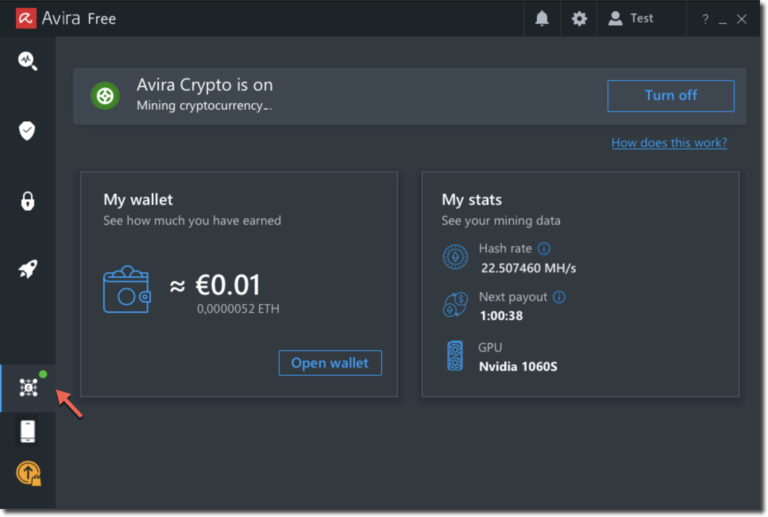
I’ve always found it alarming when something that should be protecting your computer, such as an antivirus program goes rogue, but that is exactly what
I’ve been appearing in different places in Kent for a few years now, which when it started was more than a bit confusing and laughable

Unlike the tracker tags like Tile or Apple’s AirTag, or Samsung’s SmartTag which rely on Bluetooth technology to locate a lost item and the fact
If you have given a scammer access to your computer, consider that computer compromised. It is a critical security problem, since they have had access
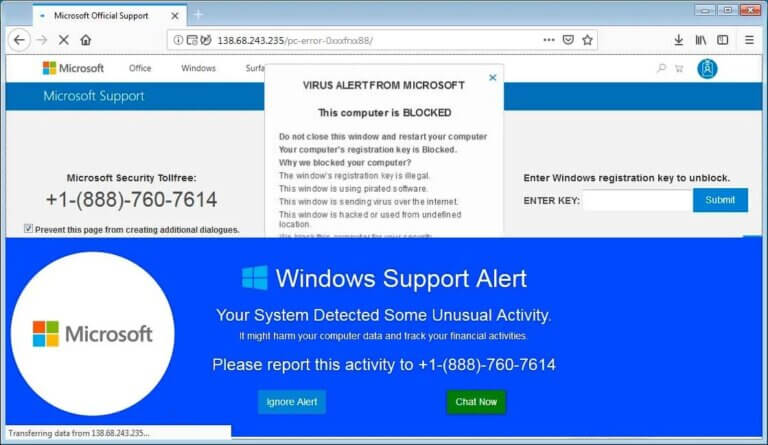
I was called out to a customer who had been scammed, but what I found was something much worse. Scammers are now using techniques gained
We all need to have passwords for everything these days, but we often can’t reuse them because reusing a password we used before leaves our

I’ve realised I’ve never made a post about Bitcoin or other cryptocurrencies. Bitcoin and other cryptocurrencies differ from normal currencies issued by countries because traditionally,

We all need help in different ways. The Internet has lots of training courses we can tap into and learn new skills. Some are free

In an ideal world, everyone would have a backup copy of all their files and folders that they can restore their computer whenever they need
Continuing the series for the #IncreaseVSChallenge for March, B is for Backup. Backups are essential for ensuring you don’t lose your precious photos or anything

Since this is the first day of March, which is the start of the #IncreaseVSChallenge. The alphabet is a word that comes from the first

Cyberstalking is a huge menace in society, since it is easy to fall foul to a stalker, be they an ex friend or someone you

There is a nasty cross browser attack that infects your computer and attempts to steal your passwords as well as giving you ads that steer

In the past, computers were simple, dumb and stupid but those days are long gone with the advent of the Internet and the ability to

When recycling and repurposing a computer, it is always best practice to wipe all data from the drive. The best way to do this is

No matter what we do, our passwords can be compromised. The trick is to create unique passwords per website, but that is difficult because we

It doesn’t seem that long ago when I built a CCTV camera for my brother in law out of a dummy camera and a Raspberry

Let’s face it, we live at a time when information is easy to find on the Internet, but so is adult content that is unsuitable
There are a few simple ways to improve Zoom meetings and video conferencing in general. Here are some simple ways to do this. From virtual