Choosing a printer
Everything you could possibly want to know about printers, how to buy and what is best value for money; what are the pitfalls and what

Everything you could possibly want to know about printers, how to buy and what is best value for money; what are the pitfalls and what
Most servers on the Internet keep the same IP address all the time, it makes life easy for their users. However, users on non-business broadband

So you want to create your own website, what is this DNS all about? When you open your web browser and type in a website,

Here are some common myths associated with websites: 1. My site will sell itself – I don’t need to advertise Having a website is like

Back in 1967, the Consumer Electronics Show was launched, and every year it shows off the latest tech every year in Las Vegas. Integrated Tech

Back in 1997, it was the Institute of Electrical and Electronic Engineers that created a standard for wireless networking we still use today. Over the
Voice technologies are becoming more powerful every day. Siri, Cortana and Google are common voice recognition services but if you need to take control of
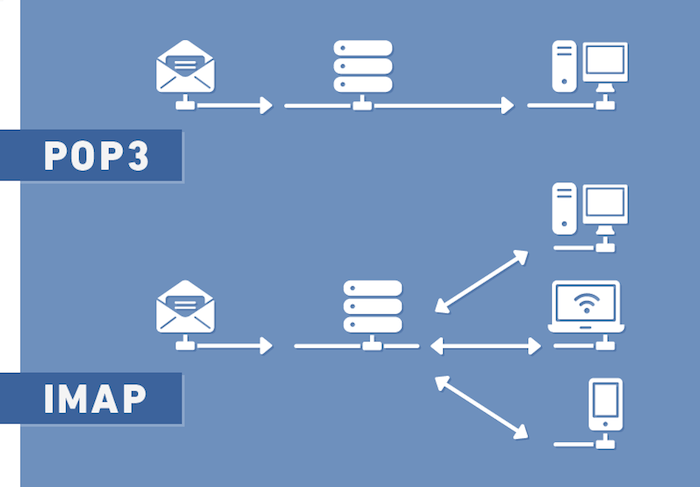
Ah the wonders of email. Now when it comes to receiving your emails from your server, you have two ways of doing that (excluding the

The Logitech K400+ is my go-to keyboard of choice when I’m repairing computers. If you have a laptop with a bad keyboard or the touch

Did you know that you can have beautiful and breathtaking views simply by opening a new tab in your browser? Tabliss for Google Chrome and
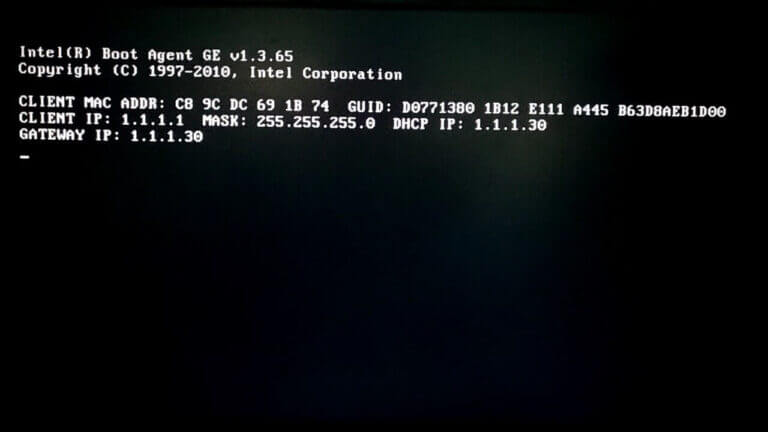
Let’s face it, reinstalling operating systems is a chore. You insert some sort of media, be that floppy disk; CD; DVD; or memory stick/flash drive

In my spare time I am reinstalling old laptops and desktop computers for Tubbs Computer Supplies so they can be given to low income families.

I have always used Trading Standards Buy With Confidence for my reviews and testimonials, however since they merged with Hampshire, I no longer get testimonials
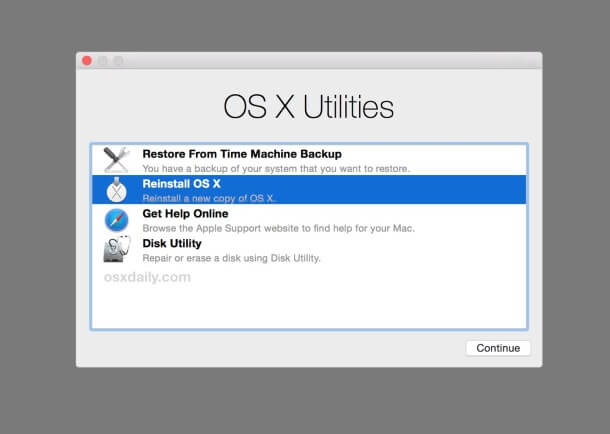
If you are considering selling your Apple Mac or need to reinstall the operating system, perhaps when installing a replacement drive or SSD. Here is

In the past there was a program called True Crypt that used to do advanced encryption. Unfortunately, during an inspection by the company there were

I’ve just received an automated phone call to my voicemail that pertains to be from HMRC. HMRC If you have ever dealt with the HMRC,

Firefox has a cool feature that protects your privacy as you use the Internet. Some websites use invisible content to track the sites you visit

Back in 2007, Apple filed a patent for Magsafe, a magnetic charger connector for their Apple laptop range. At the time, if someone tripped on

Home security can be expensive, although you can buy dummy cameras and make it look like you have security at your property, the cameras look
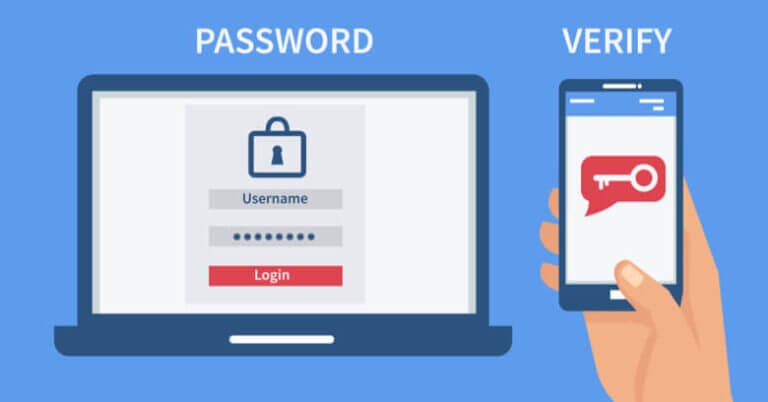
Earlier, I posted on my blog about Two Factor Authentication (2FA) using a Hardware Key. A hardware key sends a complex code on your behalf